(ABSTRACT) The power grid is evolving in the face of increasing electricity consumption and the shift towards more sustainable energy sources. However, the advancements in technology have also opened new vulnerabilities, leading to cyberattacks on the power grid. The motives behind these attacks range from financial gain to using power disruption as a mechanism of pressure. Coordinated groups of hackers, often linked to government security agencies, are responsible for these attacks. Consequences of cyberattacks include governments destabilization, financial damage, data breaches, operational disruptions, and even potential loss of life. Key assets like transformers are particularly vulnerable and can unchain a systemic failure and unstable and unwanted situations for governments and companies. To mitigate these risks, investment in physical protection systems, such as the TRANSFORMER PROTECTOR™, is crucial. By prioritizing failsafe system and implementing a Disaster Recovery Program, we can reinforce the resilience and robustness of our power grid.
As electricity consumption has grown over the past few decades, the power grid has also evolved. New technologies, devices, and the shift from traditional to newer, greener power generation are affecting an ever-expanding power grid. This has evolved from a small, isolated grid to a multinational and, at times, continental smart grid that is more complex to care for. In addition, there is now a unanimous consensus on its importance, the power system and its components are considered critical infrastructure in most countries around the world.
Thanks to technology, we can control, monitor, track and maintain our power grid and, therefore, our electricity supply. But this growing technology has widened the potential scope of action of those who want to attack this infrastructure, now considered critical, through cyber-attacks.
But how do cyberattacks occur, what are the most common motives behind these attacks, who are the organizations responsible, and what are the most likely consequences?
There are two main motives whenever these attacks occur: financial gain or attack as a constraining or intimidation tool against a company or a country.
In the first group:
- Hackers penetrate companies to extract business information, company databases and customers’ personal data.
- To freeze companies’ operations or control over their digital media. In this phase we are in a classic ransomware situation and the attack goes directly to the company’s numbers.
On the second situation, when a cyber-attack is intended to be used as a tool to intimidate or constraint against a country or a company the situation is a bit more complicated:
- These organizations intend to cut, interrupt, disturb, and damage assets and/or the entire power grid.
- In addition, during the attack, they will deploy several strategies to keep control rooms away from control or reality to prevent the attack from being stopped while it is occurring.
- Explosion of key assets can be witnessed because of induced or spontaneous changes on the power voltage.
In the latter case, the organizations or groups behind the attacks are coordinated groups of hackers, mostly linked, or related to government security agencies, as is the case with Sandworm: “According to US prosecutors and western governments, over the past decade Sandworm has been responsible for hacking operations on an astonishing scale. It has carried out numerous malign acts: political manipulation, cyber-sabotage, election interference, dumping of emails and leaking. Sandworm disabled Ukraine’s power grid in 2015. [1]” This incident knocked out power to more than 225,000 customers in three distribution-level service territories and lasted for several hours. And nowadays when we abord the conflict between Rusia and Ukraine many of the stakes are developed on the cyber space with consequences on real life.
About Cyberattacks the International Energy Agency IEA has stated: “A successful cyberattack could trigger the loss of control over devices and processes, in turn causing physical damage and widespread service disruption. In addition to the impacts on critical services, households and businesses that rely on electricity, an attack could result in millions or even billions of dollars in damages for electric utilities, including the costs of dealing with the cyberattack (i.e. detection, investigation, containment and recovery) and its consequences (e.g. from business disruption, information loss, revenue loss and equipment damage)[2]”.
Around the world, authorities have sized up the scoop on the threat and the vulnerability of the entire system: the U.S. Government Accountability Office, in an article published on 2022, already stated, “There are several points of vulnerability in the U.S.’s system of electricity grids. For example, grid distribution systems—which carry electricity from transmission systems to consumers—have grown more vulnerable, in part because their operational technology increasingly allows remote access and connections to business networks. This could allow threat actors to access those systems and potentially disrupt operations. Nations and criminal groups pose the most significant cyber threats to U.S. critical infrastructure, according to the Director of National Intelligence’s 2022 Annual Threat Assessment. These threat actors are increasingly capable of attacking the grid.[3]”
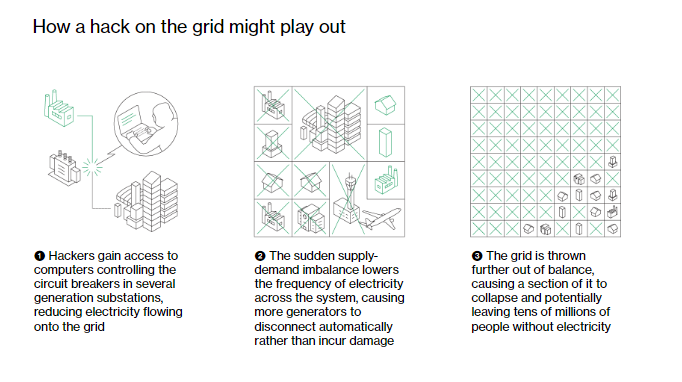

Invest in these protection and mitigation systems because the consequences are always significant. A single event of this nature can result in financial damage, civil liabilities, data breaches, loss of data, outages, loss of vision and/or loss of control of operations, loss of assets and probably loss of life.
A delicate circumstance that could transform an outage or denial of service into a more destructive incident is when key assets are compromised, damaged, and possibly exploited due to an invisible or uncontrolled overload in their flow. This scenario was already studied, and illustrated as follows: “To execute the transformer overload protection fault, the attacker needs to modify the overcurrent and thermal protection schemes… Similarly, thermal protection will not work if the circuit breaker trip setting is changed to a much higher value. DDoS attacks or traffic manipulation can block all types of alarm and trip signals from the bay level to the station level. As a result, local and regional control centers will not be able to receive any real-time information, such as transformer trips, alarms, equipment status, other system status, from the process and bay levels.“[1]
This case reveals that the consequences can be more devastating than anyone can predict; also, we learned that during a cyber-attack the company can lose sight of and control its assets; and protection schemes can be manipulated or activated. Finally, the importance of having mitigation and protection devices and strategies that can operate remotely and without constant human intervention.
A passive solution that could prevent transformer explosion due to overload has already been adopted by many utilities around the world. Thanks to its technical characteristics, it fits perfectly into any cyber-attack protection, mitigation and recovery strategy or program. The TRANSFORMER PROTECTOR™ is the only proven solution to prevent transformer explosions and fire. The TP is a passive mechanical system that cannot be hacked. According to NFPA code 850, the TP protects the tank, OLTC, bushing turrets and oil cable boxes, and is activated by dynamic pressure after short-circuiting the transformer, which guarantees its effectiveness.
The vulnerability of the power grid has been recognized widely, highlighting the need for physical protection and mitigation strategies. Implementing active and passive defense tools can help prevent cyberattacks and their potentially devastating consequences, which include financial damage, data breaches, operational disruptions and even loss of life. A major concern arises when key assets, such as transformers, are compromised, leading to more destructive incidents. It is crucial to invest in robust protection systems, such as TRANSFORMER PROTECTOR (TP), which offers a passive mechanical solution that cannot be hacked and that’s proved to prevent transformer explosions and fire, trusted by more than 2500 clients on more than 80 countries around the world.
By prioritizing passive and mechanical solutions and deploying effective disasters recovery programs, we can safeguard our power grid and ensure the reliable supply of electricity for our societies.
[1] Vulkan files leak reveals putins global and domestic cyberwarfare tactics
[2] Power systems in transition cyber resilience
[3] Securing U.S. electricity grid cyberattacks
[4] E ISAC SANS Ukraine DUC
[5] Impact Assessment of Hypothesized Cyberattacks on Interconnected Bulk Power Systems. Chee-Wooi Ten, Senior Member, IEEE, Koji Yamashita, Member, IEEE, Zhiyuan Yang, Student Member, IEEE, Athanasios V. Vasilakos, Senior Member, IEEE, and Andrew Ginter, Member, IEEE




